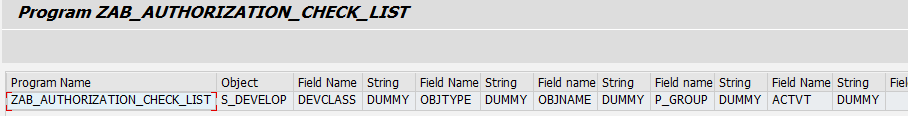
report zab_authorization_check_list.
types: begin of t_alv,
program type trdir-name,
objct type xuobject,
fiel1 type xufield,
valu1 type sstringwa,
fiel2 type xufield,
valu2 type sstringwa,
fiel3 type xufield,
valu3 type sstringwa,
fiel4 type xufield,
valu4 type sstringwa,
fiel5 type xufield,
valu5 type sstringwa,
fiel6 type xufield,
valu6 type sstringwa,
fiel7 type xufield,
valu7 type sstringwa,
fiel8 type xufield,
valu8 type sstringwa,
fiel9 type xufield,
valu9 type sstringwa,
fiel0 type xufield,
valu0 type sstringwa,
end of t_alv.
types: tt_alv type standard table of t_alv.
data: gt_alv type tt_alv.
data: gs_alv type t_alv.
data: gt_trdir type standard table of trdir.
data: gt_fcat type slis_t_fieldcat_alv.
data: gr_salv type ref to cl_salv_table.
data: gr_columns type ref to cl_salv_columns_table.
field-symbols: <trdir> type trdir.
select-options: s_prgnam for gs_alv-program.
start-of-selection.
"dummy authorization check to show the results
authority-check object 'S_DEVELOP'
id 'DEVCLASS' dummy
id 'OBJTYPE' dummy
id 'OBJNAME' dummy
id 'P_GROUP' dummy
id 'ACTVT' dummy.
if sy-subrc <> 0.
* Implement a suitable exception handling here
endif.
"select programs from trdir
select name from trdir into corresponding fields of table gt_trdir
where name in s_prgnam.
loop at gt_trdir assigning <trdir>.
perform check_authorization
using
<trdir>-name
changing
gt_alv.
endloop.
end-of-selection.
"display results
try.
call method cl_salv_table=>factory
exporting
list_display = if_salv_c_bool_sap=>false
importing
r_salv_table = gr_salv
changing
t_table = gt_alv.
catch cx_salv_msg .
endtry.
gr_columns = gr_salv->get_columns( ).
gr_columns->set_optimize( abap_true ).
gr_salv->display( ).
*&---------------------------------------------------------------------*
*& Form check_authorization
*&---------------------------------------------------------------------*
form check_authorization using f_program type trdir-name
changing ft_alv type tt_alv.
field-symbols: <token> type stoken,
<value> type any.
types: type_tokens type table of stoken ,
type_statements type table of sstmnt,
type_levels type table of slevel.
constants: c_k(30) value 'AUTHORITY-CHECK'.
data: ft_src type table of string,
ft_tokens type type_tokens ,
ft_statements type type_statements ,
ft_keywords like table of c_k,
ft_levels type type_levels ,
f_overflow(4096).
data: fs_authorization type t_alv.
data: f_prev_level type string.
data: f_fieldnr(1) type c.
data: f_fieldname type string.
data: f_lines type i.
append c_k to ft_keywords.
clear fs_authorization.
*read the source of an program
read report f_program into ft_src.
*scan source for authorizations
scan abap-source ft_src
tokens into ft_tokens
statements into ft_statements
keywords from ft_keywords
levels into ft_levels
* overflow into f_overflow
with includes
frame program from f_program
.
if sy-subrc eq 0.
describe table ft_tokens lines f_lines.
"go through results
loop at ft_tokens assigning <token>.
if sy-tabix ne 1 and <token>-str eq c_k.
fs_authorization-program = f_program.
append fs_authorization to ft_alv.
clear fs_authorization.
endif.
* if <token>-type = 'I'.
case <token>-str.
when 'AUTHORITY-CHECK'.
f_prev_level = <token>-str.
clear f_fieldnr.
when 'OBJECT'.
f_prev_level = <token>-str.
when 'ID'.
if f_fieldnr lt 9 or f_fieldnr is initial.
add 1 to f_fieldnr.
else.
f_fieldnr = 0.
endif.
f_prev_level = <token>-str.
when 'FIELD'.
f_prev_level = <token>-str.
when 'DUMMY'.
f_prev_level = <token>-str.
concatenate 'VALU' f_fieldnr into f_fieldname.
assign component f_fieldname of structure fs_authorization
to <value>.
if sy-subrc eq 0.
<value> = <token>-str.
endif.
when others.
case f_prev_level.
when 'OBJECT'.
"replace of ' marks with space
replace all occurrences of '''' in <token>-str with ' '.
condense <token>-str.
fs_authorization-objct = <token>-str.
when 'ID'.
"replace of ' marks with space
replace all occurrences of '''' in <token>-str with ' '.
condense <token>-str.
concatenate 'FIEL' f_fieldnr into f_fieldname.
assign component f_fieldname of structure fs_authorization
to <value>.
if sy-subrc eq 0.
<value> = <token>-str.
endif.
when 'FIELD'.
concatenate 'VALU' f_fieldnr into f_fieldname.
assign component f_fieldname of structure fs_authorization
to <value>.
if sy-subrc eq 0.
<value> = <token>-str.
endif.
when others.
endcase.
endcase.
if sy-tabix eq f_lines.
fs_authorization-program = f_program.
append fs_authorization to ft_alv.
clear fs_authorization.
endif.
endloop.
endif.
endform. "check_authorization